Although it may seem like something from science fiction movies, facial recognition is already a reality and has practical applications in many areas and sectors, such as security in smart buildings or access control. Knowing how does facial recognition work should be paramount in the security sector.
Facial recognition technology has undergone a great evolution in recent years, especially when executing a daily process, being able to recognize a person using an image or video.
In this text we will see what facial recognition is and how it works, showing how it is currently used in the security sector.
What is facial recognition?
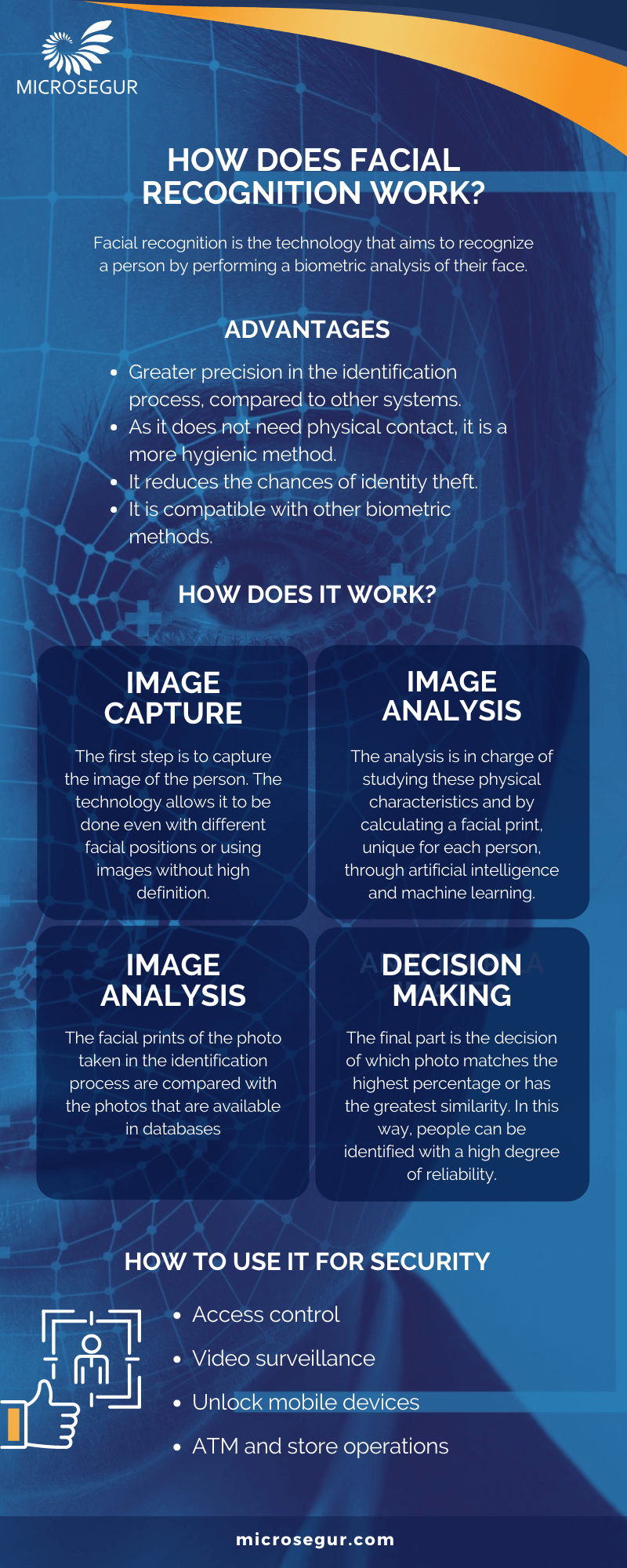
Facial recognition is the technology that aims to recognize a person by performing a biometric analysis of their face. This type of analysis takes into account the biometric characteristics of the face such as the size of the head or the distance between the eyes.
Facial recognition makes use of unique and dynamic mathematical patterns associated with each person, making this technology one of the most efficient and secure for verifying a person’s identity.
What are the advantages of facial recognition?
With the use of this technology applied to business or personal security, a series of benefits are achieved such as:
- Greater precision in the identification process, compared to other systems.
- As it does not need physical contact, it is a more hygienic method.
- It reduces the chances of identity theft, allowing you to prevent sabotage in access controls, for example.
- It is compatible with other biometric methods.

How facial recognition works
Although there are different technologies used to perform facial recognition, the general operation follows the same pattern.
Capture the image
The first step is to capture the image of the person to be identified. Although it is true that with a quality frontal image taking the best results are obtained, the advancement of this technology allows variations in the position of the face or using images without high definition to obtain reliable results.
When capturing the image, it will not be necessary to use a special photographic device, since in this technology the software used is more important.
Analyze the image
The next step is the extraction of facial characteristics to obtain biometric information and thus be able to perform an analysis and be able to form a facial biometric pattern.
In the human face there are a large number of characteristic points (nodal points) such as the distance of the eyes or the shape of the cheekbones. The analysis is in charge of studying all these characteristics (up to 80 nodal points) and in the end it will calculate a “faceprint” or facial imprint that is unique for each person.
In this analysis process, artificial intelligence and machine learning are used to achieve a high degree of reliability in the results.
Compare the picture
2D images are usually used to make the comparison, as they allow a greater and better combination and thus access databases or other sources of comparison.
In this phase, the facial prints of the photo taken in the identification process are compared with the photos that are available in databases. These databases can be private to the organization or company, or public (such as photos from Facebook or Instagram, for example).
Decision making
The final part of the process is making the decision of which photo matches the highest percentage or has the greatest similarity. In this way, people can be identified with a high degree of reliability.

How to use facial recognition in security
The use of facial recognition is more and more widespread and that is why it is common that we begin to find it in our day to day. Also knowing How does facial recognition work.
Common uses of facial recognition in security are:
Access Control
One of the most important applications, which represents a great advance for the sector, is the use of facial recognition for access control. Using this technology, companies guarantee that their employees’ access is done in a safe, fast and real way.
With the use of facial recognition in the access controls of an organization or company, it is possible to:
- Know who accesses and when.
- Guarantee access only to authorized persons.
- Accelerate work entry and exit processes.
- Control access to all facilities such as parking lots, warehouses, offices, buildings, etc.
- Avoid theft and identity theft.

Video surveillance
Within security and video surveillance, the use of facial recognition allows people to be identified automatically with a high degree of reliability. In this way, the security level is increased by easily recognizing unauthorized people, who are on a black list, and other similar situations.
State security forces use this type of technology to detect criminals using cameras in places such as airports or highways, and having their own database of photographs to compare.
Other security uses
Facial recognition is used to increase security in various aspects of our daily lives. Today we can find it in:
- Unlock mobile devices. With Face ID technology incorporated into the latest Apple mobile devices such as the iPhone or iPad, the phone can be unlocked by focusing the camera on the user’s face. This method is faster, more comfortable and more reliable than the traditional fingerprint or access code.
- Operations in ATMs and stores. Although it is not yet widespread, the use of facial recognition as a substitute for bank cards or as a payment system in stores, notably increases the security of transactions. A third party is prevented from making use of the user’s payment systems, requiring the user’s physical presence for the validation of the payment.
We have seen how does facial recognition work, a technology that has an increasing presence in security due to the different advantages it offers to organizations, companies and users. In the coming years we will see how this type of technology begins to appear regularly in our day to day.